by Tony Rushin
 CryptoLocker, “Crypto” for short, is the latest on a long, nasty list of malware that bad guys have been circulating. . This malware is a Trojan Horse (a program that masquerades as a helpful app) and also demands a ransom (another name for this type of malware is “ransomware;” I really dislike it when bad guys are the reason we add words to our urban dictionary). If you click on this malware you’ll end up with a reaction similar to the woman on the left – especially if you haven’t been doing regular backups (more on that below).
CryptoLocker, “Crypto” for short, is the latest on a long, nasty list of malware that bad guys have been circulating. . This malware is a Trojan Horse (a program that masquerades as a helpful app) and also demands a ransom (another name for this type of malware is “ransomware;” I really dislike it when bad guys are the reason we add words to our urban dictionary). If you click on this malware you’ll end up with a reaction similar to the woman on the left – especially if you haven’t been doing regular backups (more on that below).
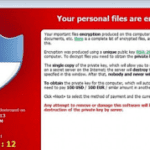 Crypto disguises itself as a legitimate-looking email with a legitimate-looking attachment. Usually the email title will read “UPS” or “Fedex” and claims to have tracking information about the status of their package. In the future I expect to see Crypto posing as an email from Amazon or other popular Christmas shopping sites. DON’T BE FOOLED! People who open the email and then click on the attachment immediately get the pop-up shown here. The message basically says: Your files are encrypted and we have the key. If you want the key it will cost you $300; otherwise you’ll never see your files again.
Crypto disguises itself as a legitimate-looking email with a legitimate-looking attachment. Usually the email title will read “UPS” or “Fedex” and claims to have tracking information about the status of their package. In the future I expect to see Crypto posing as an email from Amazon or other popular Christmas shopping sites. DON’T BE FOOLED! People who open the email and then click on the attachment immediately get the pop-up shown here. The message basically says: Your files are encrypted and we have the key. If you want the key it will cost you $300; otherwise you’ll never see your files again.
Our engineers have seen enough of this malware to substantiate that – indeed – if you click on the email attachment the bad guys immediately begin encrypting the files on your local hard drive (and sometimes on your shared drive on the Server). If you’re an attorney – or staff – in a law firm, Crypto can cause a lot of angst. As long as you’ve got your data properly backed up you can recover it, but it still means lost productivity and lost billable time. And a lot of aggravation.
How to Spot Crypto
- The email looks suspicious and looks like it’s coming from UPS, Fedex or some other popular shipping or on-line shopping site.
- If you open the email (which does NOT trigger the malware), you will see an attachment similar to the following: “tracking.pdf.exe”. Note that the file has two extensions: PDF and EXE. This isn’t normal. The bad guys put the “PDF” in there to trick you into thinking it’s legitimate. However, you should never click on an executable file (“EXE”) unless you are 100% confident about who sent it to you.
What to do if you get tricked
- Don’t panic. Shut your computer down ASAP. It may limit the damage.
- Contact your IT support professional right away.
- Your IT support professional will help you remove Crypto by running an anti-virus program (McAfee, Symantec, Kaspersky, Trend Micro). The Trojan itself is easy to remove; your files, however, are still encrypted.
- Crypto doesn’t slow down your computer like a virus does. However, your files (Word, Excel, PowerPoint, photos, etc.) are useless because you can no longer open them. With the help of your IT support professional, you will delete the encrypted (useless) files and restore your normal, non-encrypted files from your backup/recovery solution (for a home user this might be Carbonite, MozyPro, iCloud or SkyDrive).
- If you don’t have your files backed up, consider paying the ransom. It’s the only way we know for you to get the decryption key.
What to do to Avoid a Bad Situation
- Make sure you have a tried and true backup solution in place.
- At work, make sure your files are on the Server and not on your local hard drive. And make sure the files on the server are being backed up regularly.
- Use a hosted Exchange service that has a healthy Spam filter built into it to stop suspicious mail before it makes it to your inbox. For instance, our engineers have found that AppRiver’s Hosted Exchange blocks Crypto; Intermedia’s doesn’t.
- Have a physical firewall in place (SonicWALL is our firewall of choice) and have your IT support professional configure it to block Crypto (here are some home and business firewall tips).
You may be wondering, as I did, why the good guys can’t easily catch the bad guys by simply following the ransom payment trail. Unfortunately, these bad guys are really smart. The ransom payment is demanded via MoneyPak or Bitcoin – both of which use private, decentralized fund-exchange networks that are extremely difficult to trace.
 Bad guys are horrible . However, they’ve been around forever – how long ago did Cain murder Abel? I loathe bad guys and Network 1 fights against them. Do your part to fight against them, too, by recognizing malware, backing up your information and taking the proper steps to avoid malware.
Bad guys are horrible . However, they’ve been around forever – how long ago did Cain murder Abel? I loathe bad guys and Network 1 fights against them. Do your part to fight against them, too, by recognizing malware, backing up your information and taking the proper steps to avoid malware.






