by Tony Rushin
Security risks exist in any business, but for attorneys, it is exceptionally important to minimize those threats in order to protect sensitive client information. Adhering to best practices in several different areas can significantly reduce the risks of exposing private data through cyber-attacks or human error. Consider adopting these strategies to protect yourself and your clients.
Hardware and Software
- Firewalls should be present and kept up-to-date to prevent unauthorized breaches.
- High quality anti-virus and malware protection needs to be installed and regularly updated on all desktops, laptops and servers.
- Make sure that all software is actively supported and immediately utilize any available patches.
- Keep client data off of mobile devices wherever possible, and encrypt all data that is stored on laptop computers or other mobile devices.
- Create and enforce a strong mobile device management policy at your firm.
- Obtain appropriate software and learn how to remotely wipe tablets and smartphones should they be lost or stolen.
Network and Data
- Keep data well organized so that you know all of the places it exists, whether in paper form, electronic or communicated verbally.
- Ensure that backups are encrypted and stored securely, both onsite (for fast recovery) and off-site (for disaster recovery).
- Limit physical access to client data and backups.
Email and Passwords
- Never send sensitive data using Exchange Servers or consumer-based email platforms like Gmail, AOL or Yahoo. They are not secure.
- Beware of fishing attacks sent to individuals or groups of firm members. They may appear to be personal, drawing information from social media or online profiles.
- Do not download attachments or click links in emails unless you are expecting them or are certain you know and trust the sender.
- Create and follow a password policy that forbids sharing passwords.
- Don’t keep passwords on post-its attached to the computer or monitor.
- Change passwords regularly (at least quarterly).
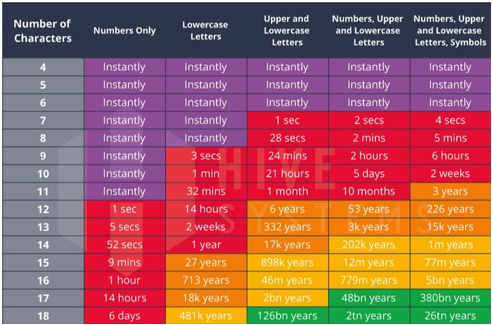
- Make sure all team members create passwords that include letters, numbers and symbols. These are far more difficult to crack than those composed of fewer elements.
Staff and Contractors
- Create a process to educate current staff as well as new hires and contractors. Make sure that policies are clearly communicated and reinforced with training.
- Issue firm-owned equipment with a standard image.
- Limit access to information to only what is needed to perform assigned tasks.
- Use checklists for onboarding and offboarding team members and contractors. This will help prevent oversights that can result in data breaches.
- Create a process to offboard employees and contractors to minimize future risk. Your firm’s process could look something like this:
- Turn in keys, badges and other equipment
- Wipe company information and email from mobile devices
- Define email rerouting, and for how long
- Apply a standard email and phone message
- Disable user id and password
- Remove from group policy
In addition to these best practices, be sure that the entire team is observing basic precautions like locking workstations before leaving a desk unattended and positioning monitors so the screen is not visible to passersby.
It’s also a good idea to get an IT security risk assessment so you’ll know where you stand and can measure your progress as you increase security. After you’ve established a baseline, document your processes and decisions for taking action (or not).
There’s no way to eliminate risk when you work with sensitive data, but following these best practices and making data security a priority will ensure that your firm is doing everything possible to safeguard your clients’ privacy.