
CloudSecureTech tells us that small businesses are 350% more susceptible to phishing attacks than large businesses.
Part of the reason is that fewer SMBs take the kind of security precautions that larger businesses take. This is a result of both the assumption that smaller businesses are less of a target and a lack of awareness of business email security best practices.
| “Advanced threat tactics aren’t reserved for enterprises. An attacker may use high-end malicious software against your small business, too.” – David Gracey, Founder & President of Network 1 Consulting |
Therefore, it is essential to understand business-grade security measures, regardless of the size of your organization. Learning how attacks may compromise your email accounts will also help you understand how to make your email messages more secure.
The rest of this article will address both factors. We will explore various types of email security attacks and discuss how your small business can enhance its threat protection.
7 Types of Email Threats Your SMB Must Beware Of
1. Phishing
Most people have heard of phishing, and many believe they are immune to it. Specifically, 90% of people feel confident they can recognize a phishing email, yet only 5% will actually pass a phishing test.
Blatant attempts at social engineering, like the “Nigerian prince” scam, are less common than they used to be. Attackers understand that such blatant attempts fool very few people, which is why modern phishing attacks are much more subtle.
Here are examples of what they look like today.
| Phishing Type | What It Does | Signs It’s In Your Email |
| Credential Harvesting Links | Emails with credential harvesting links direct users to fake login pages that mimic Microsoft 365, Google Workspace, or internal portals. The goal is to collect usernames and passwords when users try to log in. | Signs include slightly altered URLs, unexpected login prompts after clicking a link, or a request to “verify your identity” or “confirm your account” without clear context. |
| Fake Service Notifications | These emails pretend to be alerts from services your team uses. They often warn of account issues or ask you to update settings. Links in these messages usually lead to lookalike pages built to capture login credentials. | Signs include unexpected prompts to “re-verify” accounts, urgency around expiration or deactivation, and branding that is close but not exact. |
| Spoofed Domain Messages | Spoofed domain messages come from fake addresses that look nearly identical to your business or a trusted partner. Attackers might replace a single character in the domain to trick recipients into replying or clicking a malicious link. | You may notice small typos in the email address, unusual phrasing in the message, or replies to emails you never sent. These messages sometimes skip formal greetings or contain odd formatting compared to real past emails from that source. |
| Invoice Scams | Attackers impersonate vendors, clients, or executives to request payment changes or submit fake invoices. These messages often reference real projects and use a tone of urgency or confidentiality. | Red flags include new bank account details, sudden changes in payment instructions, or vendors who say they can’t take a call. |
| Executive Impersonation | These emails claim to come from the CEO, CFO, or other senior staff. Attackers often send short, urgent requests asking employees to transfer funds, buy gift cards, or share confidential data. | They may appear to come from mobile devices and lack full signatures. The tone is usually abrupt, with phrases like “Are you available?” or “I need a quick favor.” |
2. Malware-Laced Email Attachments
These emails include files that install malware when opened. The payload might log keystrokes, install remote access tools, or scan the system for sensitive data. These threats often hide behind labels like “invoice” or “purchase order,” but don’t ask for logins or mimic brands.
If one of these emails is in your inbox, you may notice vague file names, prompts to enable macros, or system instability after opening the attachment.
3. Embedded Scripts
Certain emails contain HTML files or other script-based payloads that launch attacks once opened. These may exploit unpatched email clients or browsers. The goal is to run code, collect data, or install malware without user interaction beyond opening the message.
Look for attached .html or .hta files, especially if they aren’t expected. These messages may also have little to no body content.
|
Become One of The 4,292+ Email Users That Network 1 Protects |
4. Email Bombing
Attackers send hundreds or thousands of emails to flood an inbox. This overload can prevent users from seeing genuine messages and may distract them from fraudulent transactions or unauthorized changes that are happening simultaneously.
You might see a sudden surge in newsletter signups, password reset emails, or no-content spam. In many cases, legitimate messages get buried.
5. Thread Hijacking
In a thread hijack, attackers break into an email account and reply to existing conversations with malicious content. These replies often reference past messages and appear as part of the ongoing thread.
Users might see replies from a known contact that contain unexpected attachments, vague instructions, or strange follow-up links. The message may seem rushed or slightly off in tone, primarily if the original sender is not known for brevity or urgency.
6. Spear Phishing
Spear phishing targets a specific person or group with customized, believable content. Unlike mass phishing, it uses real details (like names, job titles, or recent projects) to increase trust and avoid suspicion.
These emails often match your business tone and context. Look for urgent messages that include accurate but slightly outdated references, requests for sensitive action, or language that pressures you to respond quickly.
7. Brute Force Attacks
These attacks don’t rely on email content but target email systems directly. Attackers use automated tools to guess account credentials through repeated login attempts. If successful, they gain direct access to the inbox.
You may see login alerts from unusual locations, account lockouts, or messages sent from a user’s address without their knowledge. Admin portals may also log repeated failed login attempts.
| Explore More Key Tactics to Help Reduce Your Risk of Data Breaches |
8 Ways to Promote Secure Email For Small Business Communications
1. Require Multi-Factor Authentication
According to Microsoft, you can block 99.2% of threats by enabling multi-factor authentication (MFA). That’s because MFA makes it harder for attackers to access email, even if they have the correct password. Ensure that your MFA policy applies to all users, not just administrators.
2. Enforce Strong Password Standards
Weak or reused passwords make it easy for attackers to access business email accounts. Every user should create unique, complex passwords that are long enough to resist guessing attempts. Avoid dictionary words, personal names, or number patterns.
Business owners can reduce risk by requiring longer minimum lengths and blocking commonly used passwords.
| 💡Tip: If remembering multiple unique passwords is challenging, try creating acronyms that only you understand. For example, a password of “gHmB21G” could be an acronym of “good Humans must Be 2 1 Goal.” |
3. Apply Email Filtering Tools
Email filters can automatically detect and block spam, known malicious links, and file-based threats. Many cloud email services include built-in threat detection, but those settings must be reviewed and adjusted to fit your environment.
Small businesses should check that spam filtering is active and that suspicious messages go to quarantine instead of reaching the inbox. Regular reviews of filtered messages help confirm that important emails aren’t being blocked by mistake.
4. Set Controls For Personal Devices
Allowing staff to access business email from personal phones or laptops can be convenient, but it introduces risk if devices are not secured. Personal hardware may lack security patches, antivirus tools, or screen lock protections.
If your business supports BYOD, use policies that require secure access methods. Devices should have encryption enabled, be kept up to date, and allow remote wiping if they are lost or stolen.
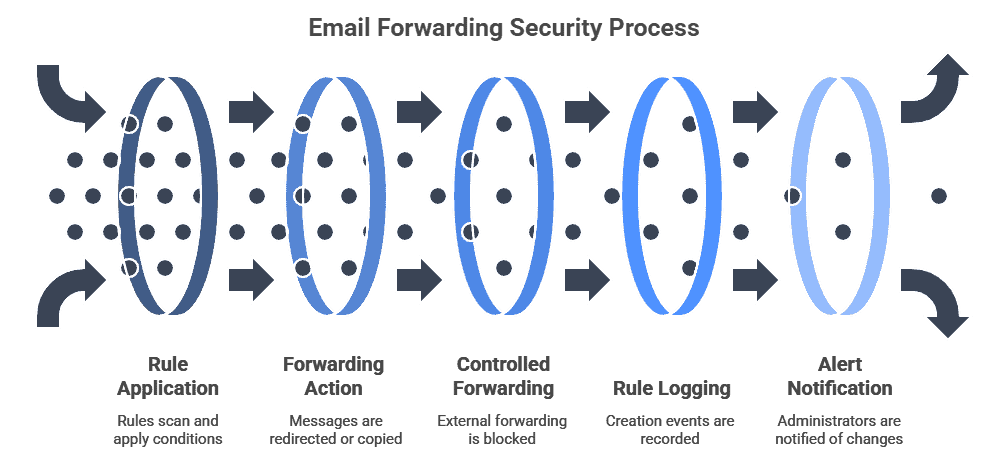
5. Control Email Forwarding
Unauthorized forwarding rules can send sensitive data to external inboxes without the user’s knowledge. Attackers often create these rules during account takeovers to stay hidden. Business owners should restrict external forwarding and review rules regularly. Admins should be notified when forwarding is enabled or changed on any mailbox.
6. Train Staff to Spot Threats
Many email threats succeed because users don’t recognize the warning signs. Business owners should schedule recurring training to help staff identify suspicious links, fake login pages, and unexpected attachments.
7. Monitor Login Activity
Unexpected sign-ins may signal a compromised account. Many platforms now offer reporting on login times, locations, and device types. Admins should check login reports regularly and set alerts for sign-ins from new devices, foreign countries, or outside business hours. These reviews can uncover suspicious behavior early.
8. Use Business-Grade Email Services
Free email platforms lack the visibility and security controls needed for professional use. Business-grade services offer better account management, audit logs, and threat protection. Small businesses should choose platforms that allow centralized management of users, MFA enforcement, spam filtering, and data loss prevention features.
| Find Atlanta-based Experts Who Can Help Improve Your Security Posture | |
| Cybersecurity Services | IT Network Support |
Get Expert Help Enhancing Your Business Email Protection
Choosing the best security solutions for your business isn’t always as easy as simply looking for the “business-grade” marker. While that is an important step, you must also realize that many business-grade options are available on the market. You need to choose one that fits seamlessly with the rest of your IT infrastructure.
If you need assistance with this process, consult the experts at Network 1 Consulting. Alongside email security solution procurement, we can also help you enhance your best practices and monitor your email systems.
Reach out to us today. Our team would be happy to answer any questions you may have.
Comments are closed for this post.










